Let's install and run RavenDB on Windows and Linux and learn how it works.
On this post we will cover:
To download your image, select Server, Stable and the appropriate version for your environment. Aaccept the terms, click on the .ZIP Package download button to download the image to your disk.
Open the Powershell terminal, cd into the folder you extract your files and run .\run.ps1 You'll then see some outputs the RavenDB service is emitting for us when running as a standalone instance:
This configuration is enough for this demo and simple development efforts. Clicking on it, RavenDB Studio will open on the default Url: http://127.0.0.1:8080/studio/index.html.
That's it! The standalone instance is running and you can start testing RavenDB on your Windows box.
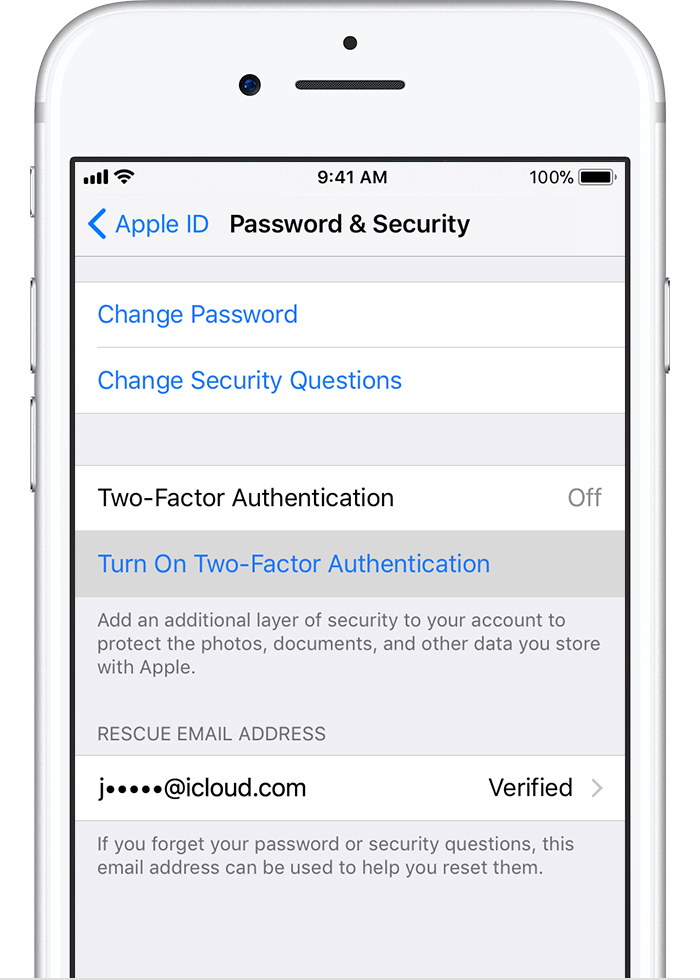
If all goes well, you'll have to accept the user license agreement and proceed with the instance configuration.
Note that:
Clicking on it, will prompt you for Http/Tcp ports and IP address. Leaving empty will use the defaults. Click "Restart Server" and RavenDB should be installed.
Get-Service -Name RavenDB
For more information, please visit: https://ravendb.net/docs/article-page/4.0/csharp/start/installation/setup-wizard
Download the image by selecting Linux x64 from the downloads page and download it using Firefox:
Once downloaded, extract the bz2 pkg on a local folder:
Cd into that folder and run "run.sh". I should then see:
For example, when I type help on my shell in Fedora, I get:
From the console, You can do things like restarting/shutting down the server, like exporting/importing data, reading logs and viewing server stats. Just type the commands shown. For example, to shut the instance down, I should type: shutdown.
Enter a DB name (for example, "Blog") and click "Create"):
Clicking on that Database creates our database and takes us to the its page. From there we basically can view our documents (records), create, query, patch, view logs, stats, etc:
Don't forget that RavenDB is also available on the cloud. Check the article An in depth review of the RavenDB Cloud for more information.
- Installing and running on Windows;
- Installing and running on Linux;
- Using the RavenDB console tool;
- Creating a new database;
Downloading RavenDB
First off, navigate to the RavenDB downloads page and download the server version for the environment you're working on. The currently supported platforms are: Windows, Linux, OSX, Raspberry PI and Docker.To download your image, select Server, Stable and the appropriate version for your environment. Aaccept the terms, click on the .ZIP Package download button to download the image to your disk.
Running standalone RavenDB on Windows
On Windows, once the download is completed, extract all those files in a folder and you'll see two PowerShell files: run.ps1 and setup-as-service.ps1.Open the Powershell terminal, cd into the folder you extract your files and run .\run.ps1 You'll then see some outputs the RavenDB service is emitting for us when running as a standalone instance:
A new window will open for you where you'll need to configure a cluster and/or security. For now, let's skip the cluster configuration and go with the Unsecure option.
That's it! The standalone instance is running and you can start testing RavenDB on your Windows box.
Installing on RavenDB Windows
To install you your machine, open the PowerShell terminal as an administrator and run the setup-as-service.ps1 script.If all goes well, you'll have to accept the user license agreement and proceed with the instance configuration.
Note that:
- the installation requires administrator privileges
- will use port 8080 for "unsecure" installs or 443 for secure (options selected during the installation)
Configuring the new Instance
After installed, you'll have to configure your instance as shows the image below. For a development setup, you should be good with the Unsecure option.Clicking on it, will prompt you for Http/Tcp ports and IP address. Leaving empty will use the defaults. Click "Restart Server" and RavenDB should be installed.
The RavenDB Service
Once installed, on Windows, we can view the service status using the Get-Service Powershell cmdlet:Get-Service -Name RavenDB
For more information, please visit: https://ravendb.net/docs/article-page/4.0/csharp/start/installation/setup-wizard
Running standalone RavenDB on Linux
The Linux installation is similar: download your Linux image from the RavenDB downloads page, unzip it and run the script. Let's see how it works.Download the image by selecting Linux x64 from the downloads page and download it using Firefox:
Once downloaded, extract the bz2 pkg on a local folder:
Cd into that folder and run "run.sh". I should then see:
Installing RavenDB on Linux
Installing RavenDB on Linux is very similar to Windows. You run the run.sh shell script and select the installation option on the command line.The RavenDB Console
After installed, basic manipulation of the server can be done either by using the Raven UI (Raven Studio) or by using the console previously opened.For example, when I type help on my shell in Fedora, I get:
From the console, You can do things like restarting/shutting down the server, like exporting/importing data, reading logs and viewing server stats. Just type the commands shown. For example, to shut the instance down, I should type: shutdown.
Creating a Database
The final needed step before touching code is to create a database. For that do: Databases -> New Database:Enter a DB name (for example, "Blog") and click "Create"):
Clicking on that Database creates our database and takes us to the its page. From there we basically can view our documents (records), create, query, patch, view logs, stats, etc:
Next Steps
Now that RavenDB is running and the database is created, the next step is to start interacting with it. You can use either RavenDB Studio or the client Api (with C#, Java, Python, etc). For more details, check my simple introduction to RavenDB.Don't forget that RavenDB is also available on the cloud. Check the article An in depth review of the RavenDB Cloud for more information.
Conclusion
Hope this post shows how is a simple introduction on how to install RavenDB on Windows and Linux boxes. For more information, check the official documentation.References
See Also
- My journey to 1 million articles read
- Creating ASP.NET Core websites with Docker
- Send emails from ASP.NET Core websites using SendGrid and Azure
- A simple introduction to RavenDB
- An in depth review of the RavenDB Cloud
- Why I use Fedora Linux
- Running RavenDB on Docker
- Querying RavenDB Metadata
- Patching RavenDB Metadata